An error occurred
Product Catalog
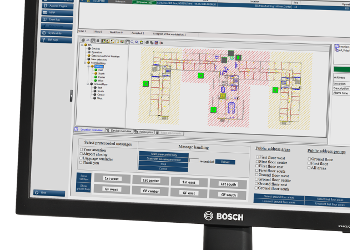
The product portfolio includes video surveillance, intrusion detection, fire detection and voice evacuation systems as well as access control and management systems. Professional audio and conference systems for communication of voice, sound and music complete the range.